Security gaps in virtualized apps
Introduction
Almost all mobile apps are designed to run natively on our mobile phones without the need to add any virtualization software. The underlining OS handles resources and the necessary infrastructure to run apps securely. In Android, every app is assigned a unique UID upon process initialization providing it an isolated view of the system and protection not to interfere with other apps and data.
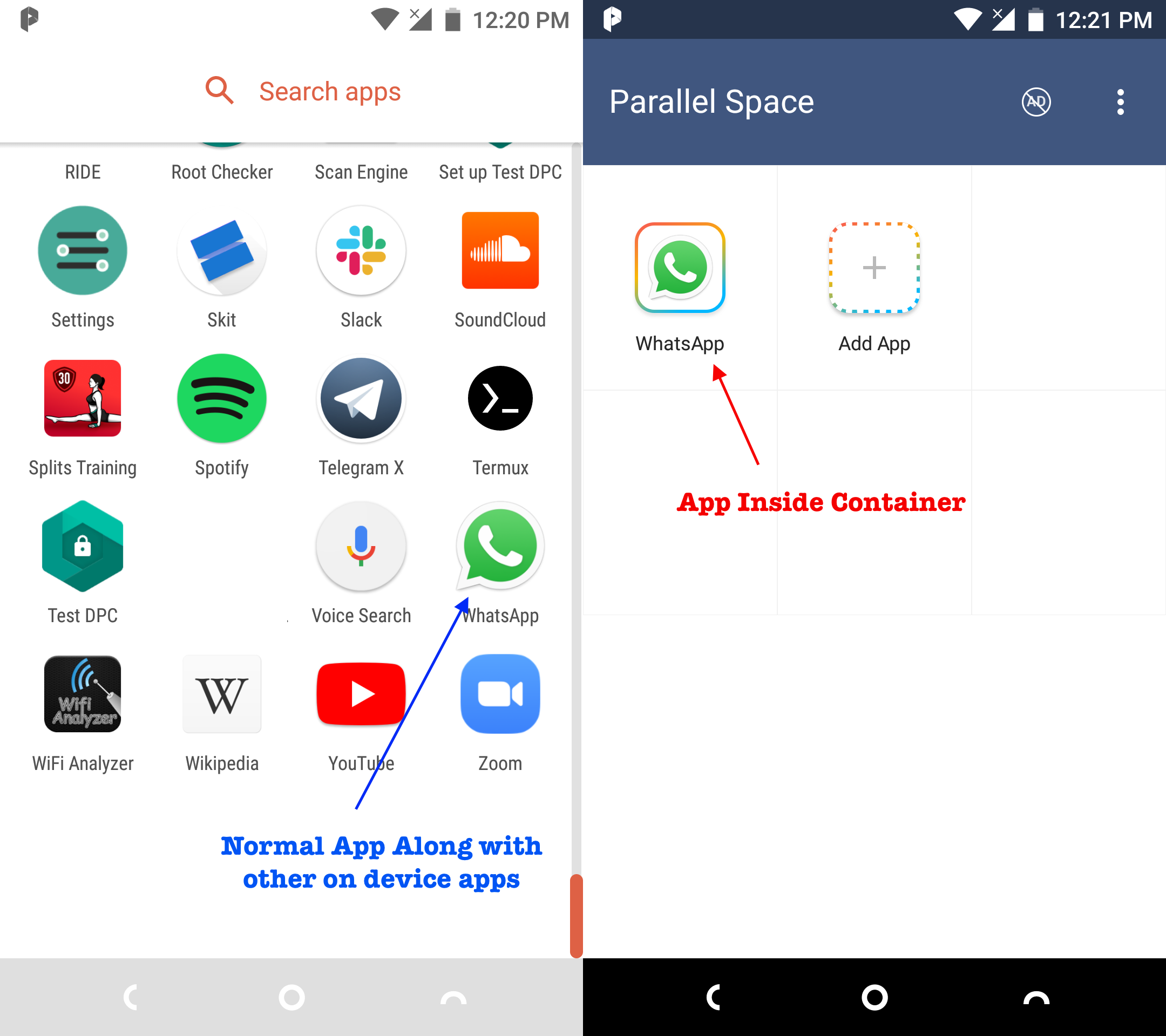
There are few virtualization apps (some even on GooglePlay - e.g. Parallel Space) that allow users to clone apps in a virtual environment. The process involves copying/cloning an existing app from the device and installing it in a virtualized environment. The common use-case allows users to install the same two apps simultaneously/side-by-side. E.g. WhatsApp personal, WhatsApp personal 2 number, WhatsApp personal 3 number, etc
Risks
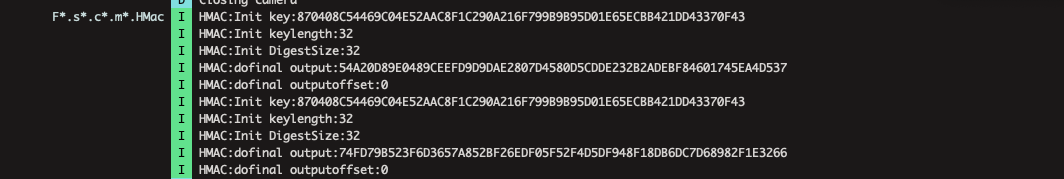
There is a detailed blog & talk given on this subject by Arvind. You can refer to his blog here, https://darvincitech.wordpress.com/2020/07/18/all-your-crypto-keys-belongs-to-me-in-android-virtual-containers. Since containerized apps are controlled by the virtualizing app, there are serious implications for apps that need a very secure environment to operate. One such case is attacking Android’s cryptographic APIs and hijacking key-pairs used by these apps. We will see one example in action below
POC
The blog takes Azure authenticator app and modifies it so that the OTP generated can be compromised allowing attackers to bypass OTP secured internet account. On his blog, Arvind showed the vulnerability in action but there were few crashes because the app checks its signing certificate as a defense mechanism. Here I wanted to build upon this work and modify the app so that the POC works end-to-end without a crash, creating a more complete (and hopefully - scarier 😎) demo.
The process involves the following steps
Install virtualized app - Arvind conveniently open-sourced a modified version that injects fake security provider that replaces the system’s default crypto provider. This is critical because extracting OTP tokens happens inside this layer. https://github.com/darvincisec/VirtualDynamicAnalysis
Install the modified version of Azure authenticator. I don’t want to publish this sensitive binary at the moment unless it’s for research purposes. If you need one email me at sirackh[at]gmail[dot]com
Setup your Authenticator and attempt to sign in from your desktop or mobile. You will see a logcat output with the sensitive credentials printed.